- Understanding TLS and SSL
- What is mTLS?
- How mTLS Works
- Benefits of mTLS
- Use Cases for mTLS
- Implementing mTLS
- Troubleshooting mTLS
- Conclusion and further reading
Mutual TLS (mTLS) is a security protocol that enhances the standard Transport Layer Security (TLS) by requiring both the client and the server to authenticate each other. This bidirectional authentication provides an additional layer of security, ensuring that both parties in a communication session are verified and trusted. This article will delve into the details of mTLS, explaining its benefits, use cases, and implementation.
Understanding TLS and SSL
Before diving into mTLS, it's essential to understand TLS and its predecessor, Secure Sockets Layer (SSL). TLS is a cryptographic protocol designed to provide secure communication over a computer network. It is widely used for securing web traffic, email, messaging, and other forms of communication.
TLS ensures three key aspects of secure communication:
- Encryption: Ensures that data transmitted between the client and server is unreadable by unauthorized parties.
- Integrity: Guarantees that data is not altered during transmission.
- Authentication: Verifies the identity of the communicating parties.
In standard TLS, the server is authenticated by the client using a server certificate, but the client is not authenticated by the server. This is where mTLS comes into play.
What is mTLS?
mTLS extends the standard TLS protocol by adding client authentication to the process. In mTLS, both the client and the server present certificates to authenticate each other. This mutual authentication ensures that both parties involved in the communication are trusted entities.
How mTLS Works
The mTLS handshake involves several steps, similar to the TLS handshake but with additional client authentication. Here’s a step-by-step overview of the mTLS handshake process:
- Client Hello: The client initiates the handshake by sending a "Client Hello" message, which includes the supported cipher suites and the client's random value.
- Server Hello: The server responds with a "Server Hello" message, selecting a cipher suite and sending the server's random value.
- Server Certificate: The server sends its certificate to the client to prove its identity.
- Client Certificate Request: The server requests a certificate from the client to authenticate the client.
- Server Hello Done: The server signals the end of its part of the handshake.
- Client Certificate: The client sends its certificate to the server.
- Client Key Exchange: The client generates a pre-master secret, encrypts it with the server’s public key, and sends it to the server.
- Client Certificate Verify: The client sends a digitally signed message to the server, proving the ownership of the client certificate.
- Finished Messages: Both the client and server exchange "Finished" messages to verify that the handshake was successful and that they have the same session keys.
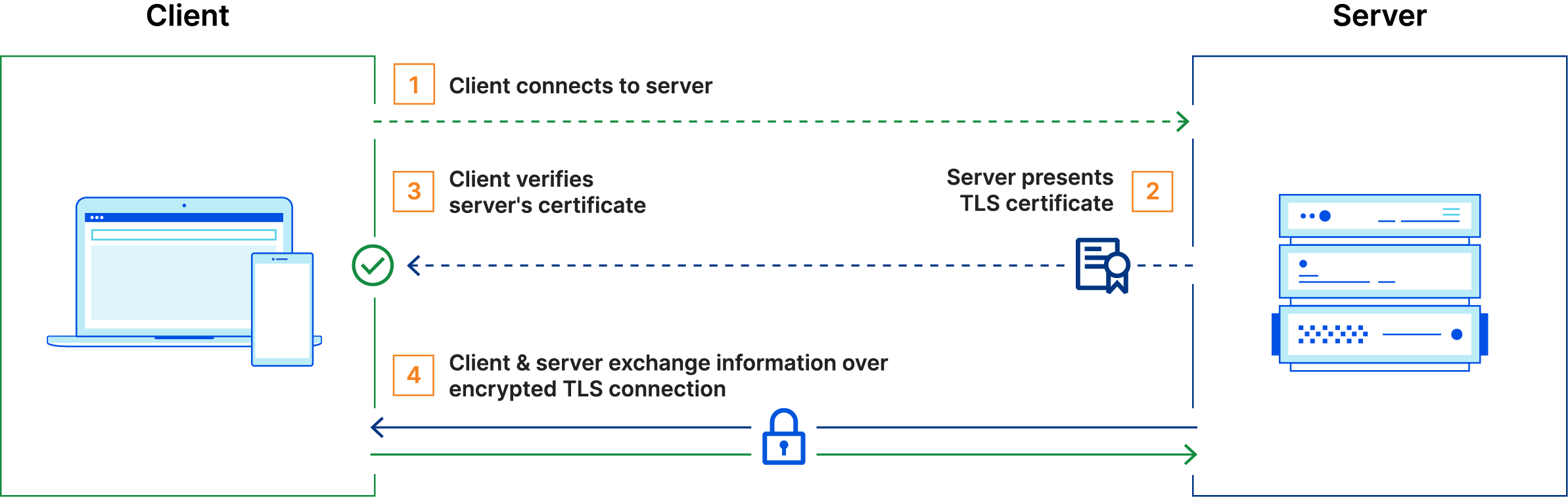
After the handshake is complete, a secure and authenticated communication channel is established between the client and the server.
Benefits of mTLS
mTLS provides several advantages over standard TLS:
- Enhanced Security: By requiring both the client and the server to authenticate each other, mTLS ensures that only trusted parties can communicate. This prevents man-in-the-middle attacks and unauthorized access.
- Compliance: Many industries have strict regulatory requirements for secure communication, and mTLS can help meet these requirements by providing strong authentication mechanisms.
- Zero Trust Architecture: mTLS is a key component of Zero Trust security models, where every entity, regardless of its location, must be authenticated and authorized before accessing resources.
- Data Integrity and Confidentiality: mTLS ensures that data remains confidential and is not tampered with during transmission.
Use Cases for mTLS
mTLS is particularly useful in scenarios where secure and authenticated communication is critical. Some common use cases include:
- API Security: mTLS is often used to secure API communications, ensuring that only authorized clients and servers can access and interact with the API.
- Microservices: In a microservices architecture, mTLS can secure communication between services, ensuring that only authenticated services can communicate with each other.
- Internet of Things (IoT): mTLS can be used to secure communication between IoT devices and backend servers, ensuring that only trusted devices can send data to the server.
- Financial Services: Financial institutions use mTLS to secure communication between systems, ensuring that sensitive financial data is protected.
Implementing mTLS
Implementing mTLS involves configuring both the server and the client to use certificates for mutual authentication. Here are the general steps for setting up mTLS:
1. Generate Certificates
Both the server and the client need certificates issued by a trusted Certificate Authority (CA). You can use a commercial CA or set up your own CA using tools like OpenSSL.
# Generate CA key and certificate
openssl genrsa -out ca.key 2048
openssl req -x509 -new -nodes -key ca.key -sha256 -days 3650 -out ca.crt
# Generate server key and CSR
openssl genrsa -out server.key 2048
openssl req -new -key server.key -out server.csr
# Sign server certificate with CA
openssl x509 -req -in server.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out server.crt -days 365 -sha256
# Generate client key and CSR
openssl genrsa -out client.key 2048
openssl req -new -key client.key -out client.csr
# Sign client certificate with CA
openssl x509 -req -in client.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out client.crt -days 365 -sha256
2. Configure the Server
The server needs to be configured to request and verify client certificates. The exact configuration depends on the server software you are using. Here’s an example for an Nginx server:
server {
listen 443 ssl;
server_name example.com;
ssl_certificate /path/to/server.crt;
ssl_certificate_key /path/to/server.key;
ssl_client_certificate /path/to/ca.crt;
ssl_verify_client on;
location / {
# Your application configuration
}
}
For Apache, the configuration would look like this:
<VirtualHost *:443>
ServerName example.com
SSLEngine on
SSLCertificateFile /path/to/server.crt
SSLCertificateKeyFile /path/to/server.key
SSLCACertificateFile /path/to/ca.crt
SSLVerifyClient require
SSLVerifyDepth 1
<Location />
# Your application configuration
</Location>
</VirtualHost>
3. Configure the Client
The client needs to present its certificate when establishing a connection with the server. The configuration varies depending on the client software or library being used. Here’s an example using cURL:
curl --cert /path/to/client.crt --key /path/to/client.key --cacert /path/to/ca.crt https://example.com
For a Python client using the requests library:
import requests
url = 'https://example.com'
cert = ('/path/to/client.crt', '/path/to/client.key')
ca_cert = '/path/to/ca.crt'
response = requests.get(url, cert=cert, verify=ca_cert)
print(response.text)
Troubleshooting mTLS
Implementing mTLS can sometimes be challenging. Here are some common issues and troubleshooting tips:
- Certificate Errors: Ensure that the certificates are correctly generated and signed by a trusted CA. Verify the certificate paths in the configuration files.
- Client Authentication Failure: Make sure the client certificate is valid and trusted by the server. Check the server logs for more details on the failure.
-
Network Issues: Ensure that there are no network issues preventing the client and server from communicating. Use tools like
telnetorncto test connectivity.
Conclusion and further reading
mTLS is a powerful security protocol that enhances the standard TLS by adding mutual authentication. It ensures that both the client and the server are trusted entities, providing a higher level of security for sensitive communications. By understanding the benefits, use cases, and implementation details of mTLS, you can secure your applications and systems against various threats.
For more information, you can refer to the following resources:


